TheHive Project


Room Outline
Welcome to TheHive Project Outline!
This room will cover the foundations of using the TheHive Project, a Security Incident Response Platform.
Specifically, we will be looking at:
What TheHive is?
An overview of the platform's functionalities and integrations.
Installing TheHive for yourself.
Navigating the UI.
Creation of a case assessment.
Before we begin, ensure you download the attached file, as it will be needed for Task 5.

Introduction
TheHive Project is a scalable, open-source and freely available Security Incident Response Platform, designed to assist security analysts and practitioners working in SOCs, CSIRTs and CERTs to track, investigate and act upon identified security incidents in a swift and collaborative manner.
Security Analysts can collaborate on investigations simultaneously, ensuring real-time information pertaining to new or existing cases, tasks, observables and IOCs are available to all team members.
More information about the project can be found on https://thehive-project.org/ & their GitHub Repo.
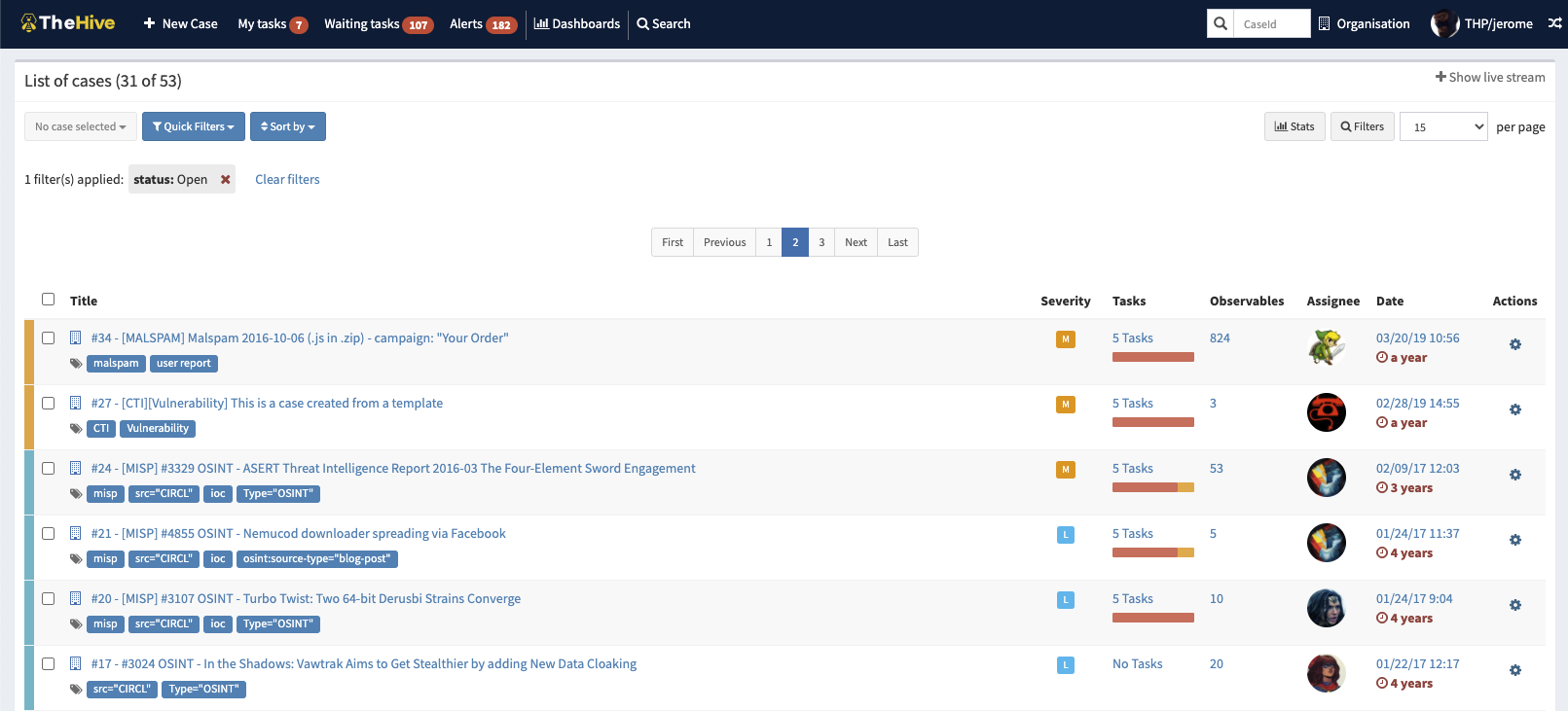
Image: Cases dashboard on TheHive by order of reported severity
TheHive Project operates under the guide of three core functions:
Collaborate: Multiple analysts from one organisation can work together on the same case simultaneously. Through its live stream capabilities, everyone can keep an eye on the cases in real time.
Elaborate: Investigations correspond to cases. The details of each case can be broken down into associated tasks, which can be created from scratch or through a template engine. Additionally, analysts can record their progress, attach artifacts of evidence and assign tasks effortlessly.
Act: A quick triaging process can be supported by allowing analysts to add observables to their cases, leveraging tags, flagging IOCs and identifying previously seen observables to feed their threat intelligence.
TheHive Features & Integrations
TheHive allows analysts from one organisation to work together on the same case simultaneously. This is due to the platform's rich feature set and integrations that support analyst workflows. The features include:
Case/Task Management: Every investigation is meant to correspond to a case that has been created. Each case can be broken down into one or more tasks for added granularity and even be turned into templates for easier management. Additionally, analysts can record their progress, attach pieces of evidence or noteworthy files, add tags and other archives to cases.
Alert Triage: Cases can be imported from SIEM alerts, email reports and other security event sources. This feature allows an analyst to go through the imported alerts and decide whether or not they are to be escalated into investigations or incident response.
Observable Enrichment with Cortex: One of the main feature integrations TheHive supports is Cortex, an observable analysis and active response engine. Cortex allows analysts to collect more information from threat indicators by performing correlation analysis and developing patterns from the cases. More information on Cortex.
Active Response: TheHive allows analysts to use Responders and run active actions to communicate, share information about incidents and prevent or contain a threat.
Custom Dashboards: Statistics on cases, tasks, observables, metrics and more can be compiled and distributed on dashboards that can be used to generate useful KPIs within an organisation.
Built-in MISP Integration: Another useful integration is with MISP, a threat intelligence platform for sharing, storing and correlating Indicators of Compromise of targeted attacks and other threats. This integration allows analysts to create cases from MISP events, import IOCs or export their own identified indicators to their MISP communities.
Malware Information Sharing Platform is is an open-source threat information platform used to facilitate the collection and sharing of threat information.
Other notable integrations that TheHive supports are DigitalShadows2TH & ZeroFox2TH, free and open-source extensions of alert feeders from DigitalShadows and ZeroFox respectively. These integrations ensure that alerts can be added into TheHive and transformed into new cases using pre-defined incident response templates or by adding to existing cases.
Answer the questions below
Which open-source platform supports the analysis of observables within TheHive?
Cortex
User Profiles & Permissions
TheHive offers an administrator the ability to create an organisation group to identify the analysts and assign different roles based on a list of pre-configured user profiles.
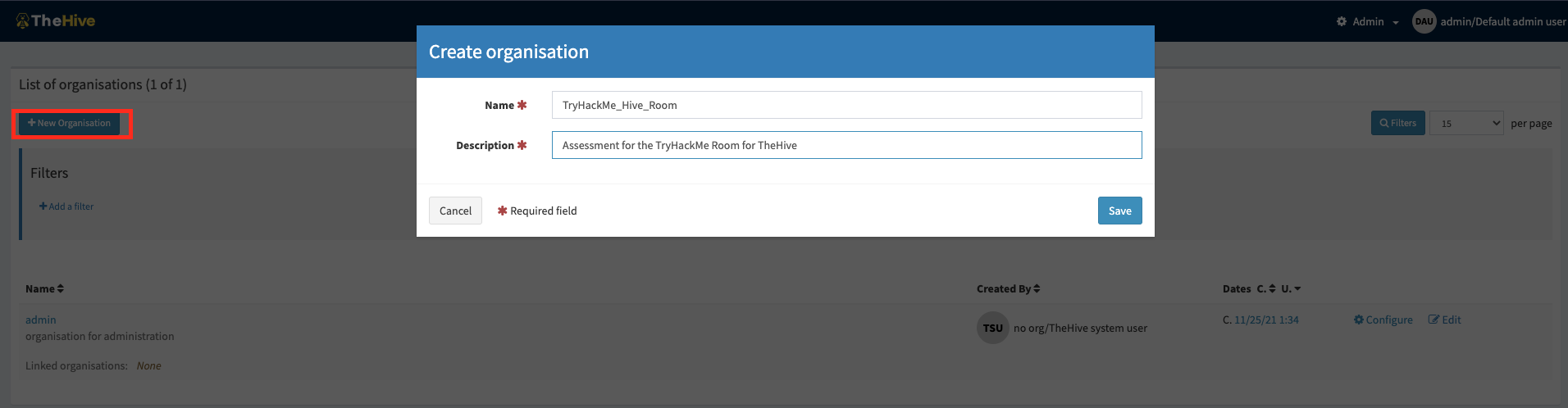
Admin Console - Create Organisation
The pre-configured user profiles are:
admin: full administrative permissions on the platform; can't manage any Cases or other data related to investigations;
org-admin: manage users and all organisation-level configuration, can create and edit Cases, Tasks, Observables and run Analysers and Responders;
analyst: can create and edit Cases, Tasks, Observables and run Analysers & Responders;
read-only: Can only read, Cases, Tasks and Observables details;
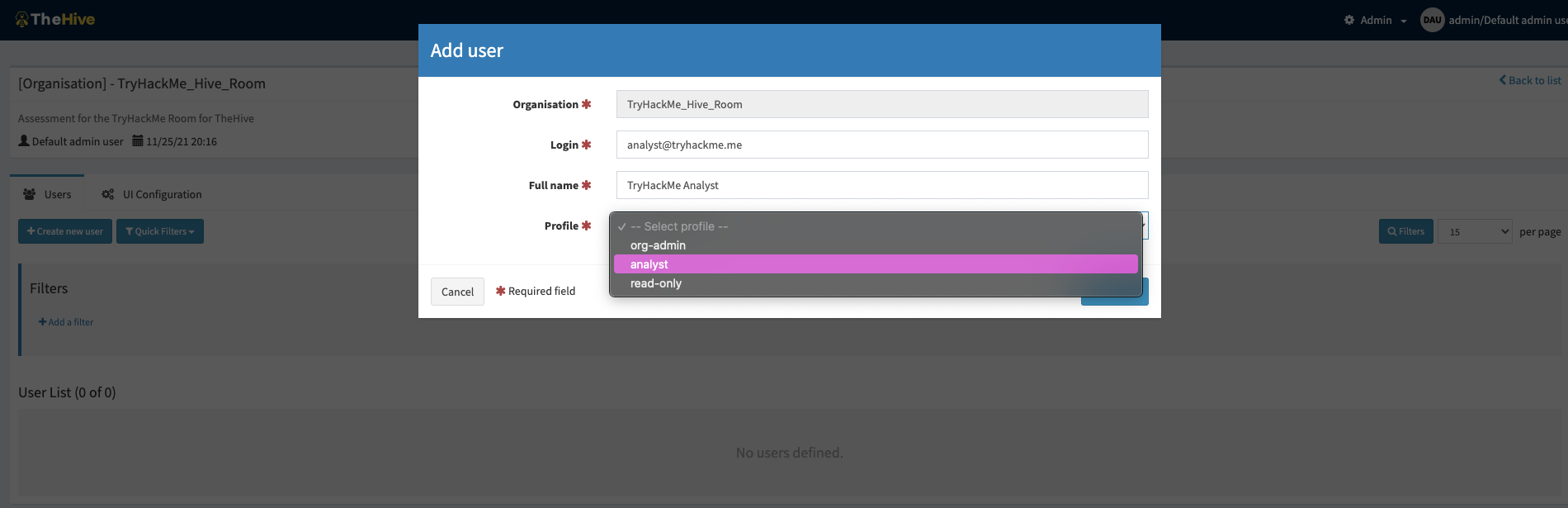
Admin Console - Add User
Each user profile has a pre-defined list of permissions that would allow the user to perform different tasks based on their role. When a profile has been selected, its permissions will be listed.
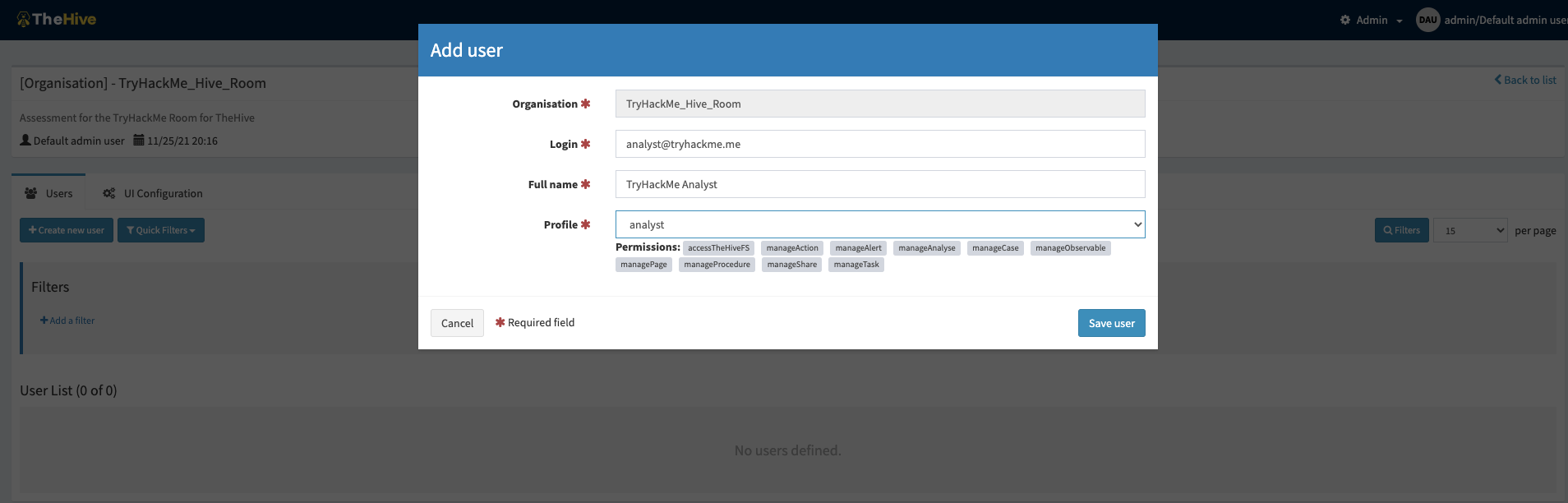
The full list of permissions includes:
Permission
Functions
**manageOrganisation (1) **
Create & Update an organisation
**manageConfig (1) **
Update Configuration
**manageProfile (1) **
Create, update & delete Profiles
**manageTag (1) **
Create, update & Delete Tags
**manageCustomField (1) **
Create, update & delete Custom Fields
**manageCase **
Create, update & delete Cases
**manageObservable **
Create, update & delete Observables
**manageALert **
Create, update & import Alerts
**manageUser **
Create, update & delete Users
**manageCaseTemplate **
Create, update & delete Case templates
**manageTask **
Create, update & delete Tasks
manageShare
Share case, task & observable with other organisations
**manageAnalyse (2) **
Execute Analyse
**manageAction (2) **
Execute Actions
**manageAnalyserTemplate (2) **
Create, update & delete Analyser Templates
Note that (1) Organisations, configuration, profiles and tags are global objects. The related permissions are effective only on the “admin” organisation. (2) Actions, analysis and template are available only if the Cortex connector is enabled.
In addition to adding new user profiles, the admin can also perform other operations such as creating case custom fields, custom observable types, custom analyser templates and importing TTPs from the MITRE ATT&CK framework, as displayed in the image below.
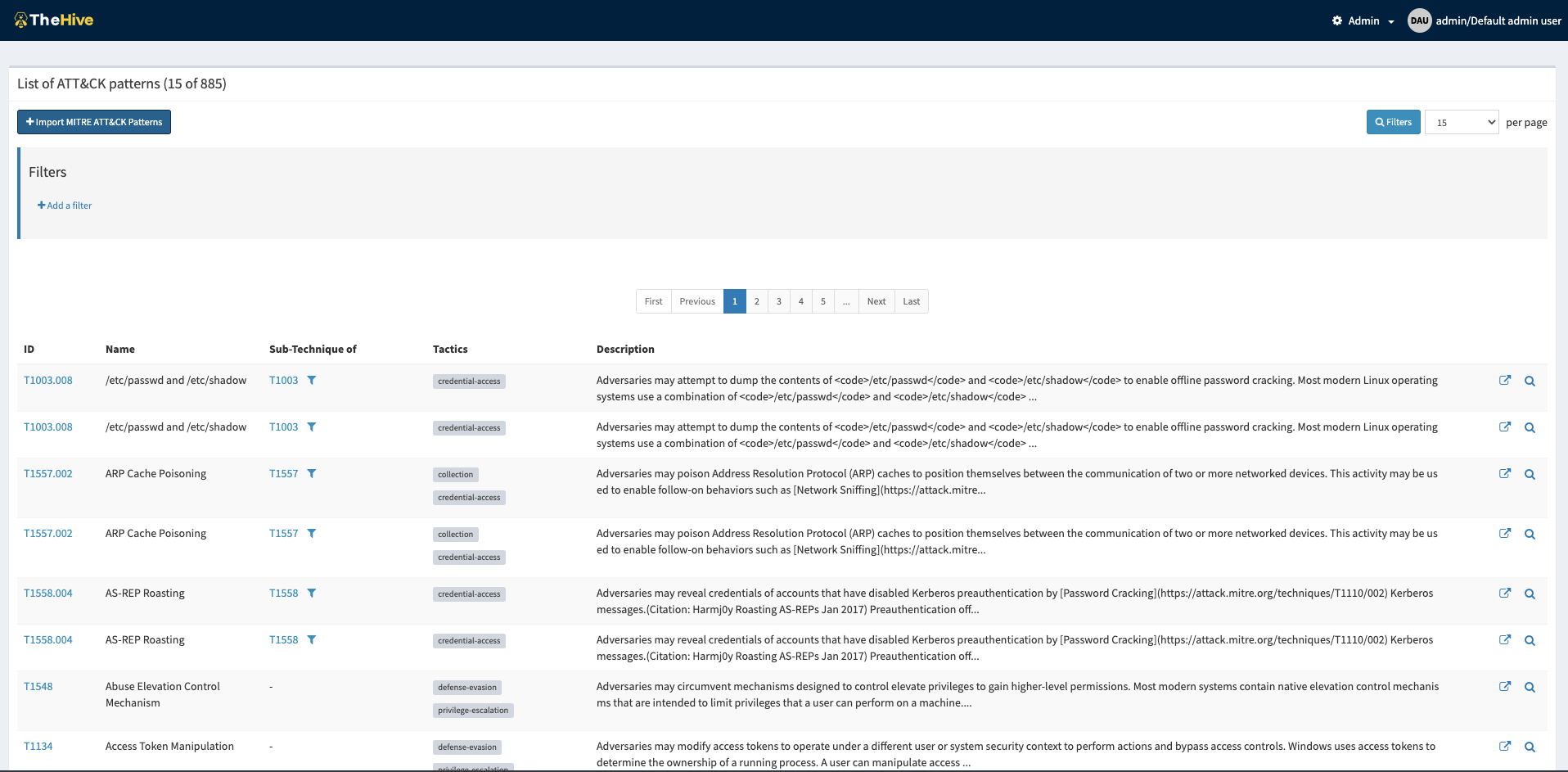
Imported list of ATT&CK Patterns
Deploy the machine attached to follow along on the next task. Please give it a minimum of 5 minutes to boot up. It would be best if you connected to the portal via http://MACHINE_IP/index.html on the AttackBox or using your VPN connection.
Log on to the analyst profile using the credentials:
Username: analyst@tryhackme.me Password: analyst1234
Answer the questions below
Which pre-configured account cannot manage any cases?
admin
Which permission allows a user to create, update or delete observables?
manageObservable
Which permission allows a user to execute actions?
manageAction
Analyst Interface Navigation
SCENARIO
You have captured network traffic on your network after suspicion of data exfiltration being done on the network. This traffic corresponds to FTP connections that were established. Your task is to analyse the traffic and create a case on TheHive to facilitate the progress of an investigation. If you are unfamiliar with using Wireshark, please check out this room first and come back to complete this task.
Source of PCAP file: IntroSecCon CTF 2020
Once an analyst has logged in to the dashboard, they will be greeted with the screen below. At the top, various menu options are listed that allow the user to create new cases and see their tasks and alerts. A list of active cases will be populated on the centre console when analysts create them.
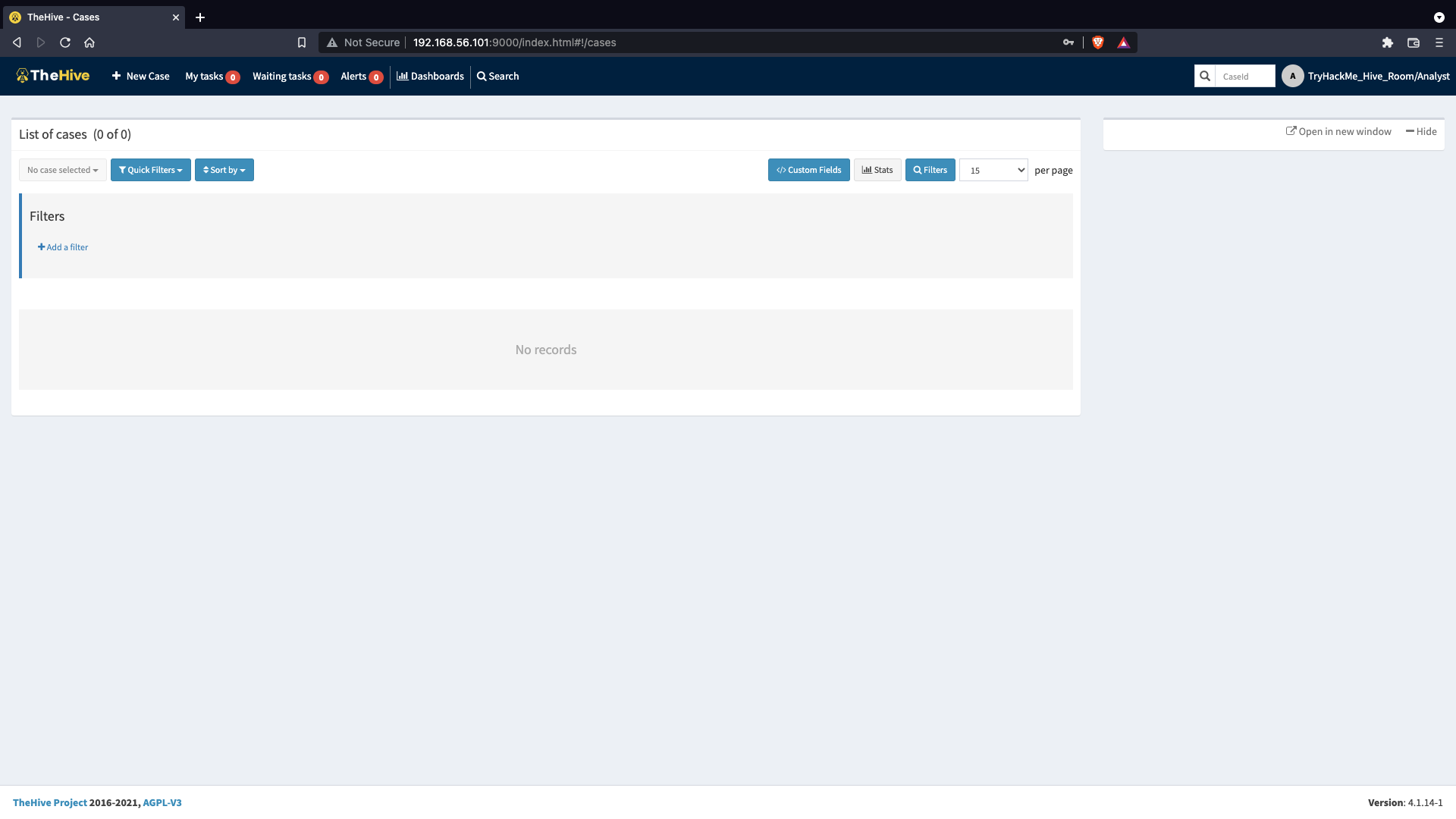
Image: TheHive Main Landing Page
On clicking theNew Case tab, a pop-up window opens, providing the analyst with fields to input their case details and tasks. The following options must be indicated on the case to set different categories and filter options:
Severity: This showcases the level of impact the incident being investigated has on the environment from low to critical levels.
TLP: The Traffic Light Protocol is a set of designations to ensure that sensitive information is shared with the appropriate audience. The range of colours represents a scale between full disclosure of information (White) and No disclosure/ Restricted (Red). You can find more information about the definitions on the CISA website.
PAP: The Permissible Actions Protocol is used to indicate what an analyst can do with the information, whether an attacker can detect the current analysis state or defensive actions in place. It uses a colour scheme similar to TLP and is part of the MISP taxonomies.
With this in mind, we open a new case and fill in the details of our investigation, as seen below. Additionally, we add a few tasks to the case that would guide the investigation of the event.
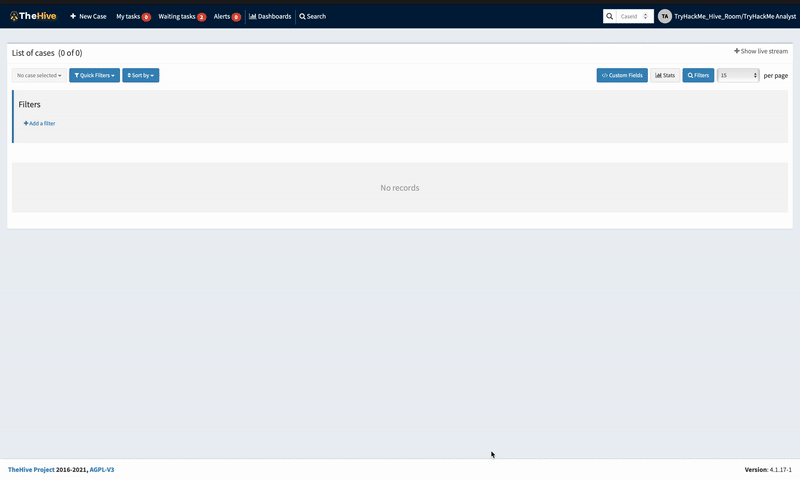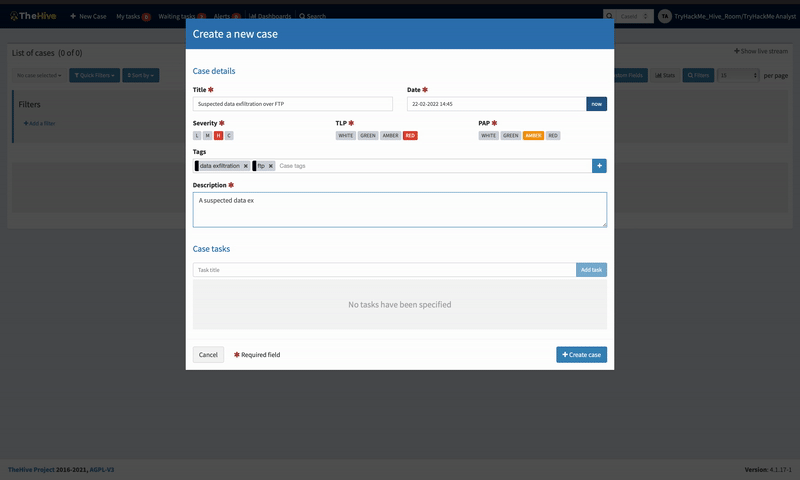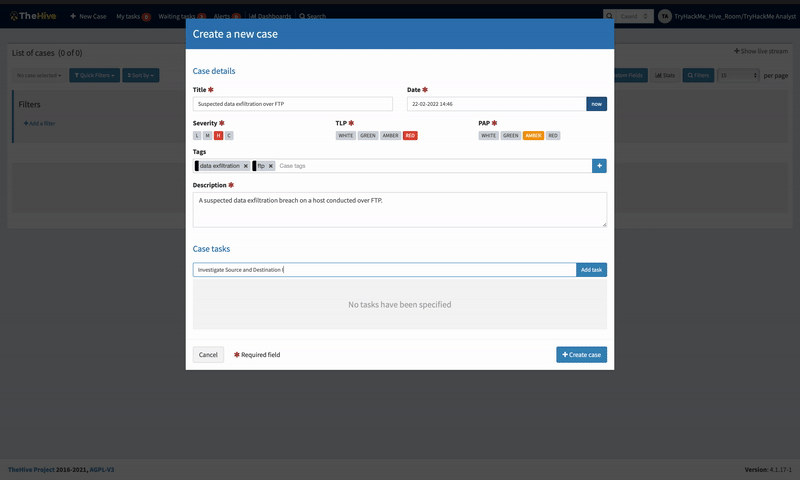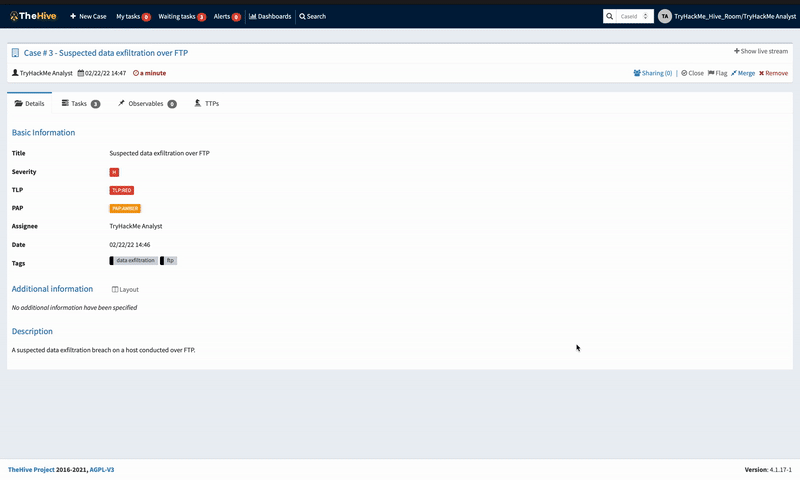
New Case Window
In the visual below, we add the corresponding tactic and technique associated with the case. This provides additional information that can be helpful to map out the threat. As this is an exfiltration investigation, that is the specific tactic chosen and followed by the specific T1048.003 technique for Exfiltration Over Unencrypted/Obfuscated Non-C2 Protocol.

TTPs Selection Window
Case observables will be added from the Observables tab and you would have to indicate the following details:
Field
Description
Examples
Type *:
The observable dataType
IP address, Hash, Domain
Value *:
Your observable value
8.8.8.8, 127.0.0.1
One observable per line:
Create one observable per line inserted in the value field.
One single multiline observable:
Create one observable, no matter the number of lines
Long URLs
TLP *:
Define here the way the information should be shared.
Is IOC:
Check if this observable is considered an Indicator of Compromise
Emotet IP
Has been sighted:
Has this observable been sighted on your information system?
Ignore for similarity:
Do not correlate this observable with other similar observables.
Tags **:
Insightful information Tags.
Malware IP; MITRE Tactics
Description **:
Description of the observable
In our scenario, we are adding the IP address 192... as our observable as this IP is the source of the FTP requests. Depending on the situation of your analysis, this observable can be marked as an IOC or if it has been sighted before in a different investigation.

New Observables Window
Answer the questions below
Where are the TTPs imported from?
A globally-accessible knowledge base of adversary tactics and techniques based on real-world observations.
MITRE ATT&CK Framework
According to the Framework, what type of Detection "Data source" would our investigation be classified under?
Research on the TTP assigned

Network Traffic
Upload the pcap file as an observable. What is the flag obtained fromhttps://10.10.82.47//files/flag.html


http://10.10.82.47/files/flag.html

THM{FILES_ARE_OBSERVABLERS}
Room Conclusion
We have now reached the end of TheHive Project room.
This room has hopefully given you a good grasp of how incident response and management is performed using TheHive and give you a working knowledge of the tool.
You are advised to experiment with these foundations until you are completely comfortable with them and to open up to more experiments with the mentioned integrations and others.
[[Velociraptor]]
Last updated